Introduction
Sharing sensitive information on the internet has always been a challenge. Ideally information would be shared securely with the intended audience once and disappear there after. This is why we created our One-Time Secret service. There are many ways to interact with our service, whether it is through our website, CLI tool, or API.
This service allows users to optionally password protect sensitive information. A unique link is generated to distribute the secret. Once the secret is opened once, it is no longer available to view again. If the secret is never viewed, it expires by itself.
Using our website
This is probably the easiest way to interact with our One-Time Secret service. Simply go to secret.jetrails.com and you will be greeted with a form to create a password. Simply fill it out with whatever properties you want your secret to have.
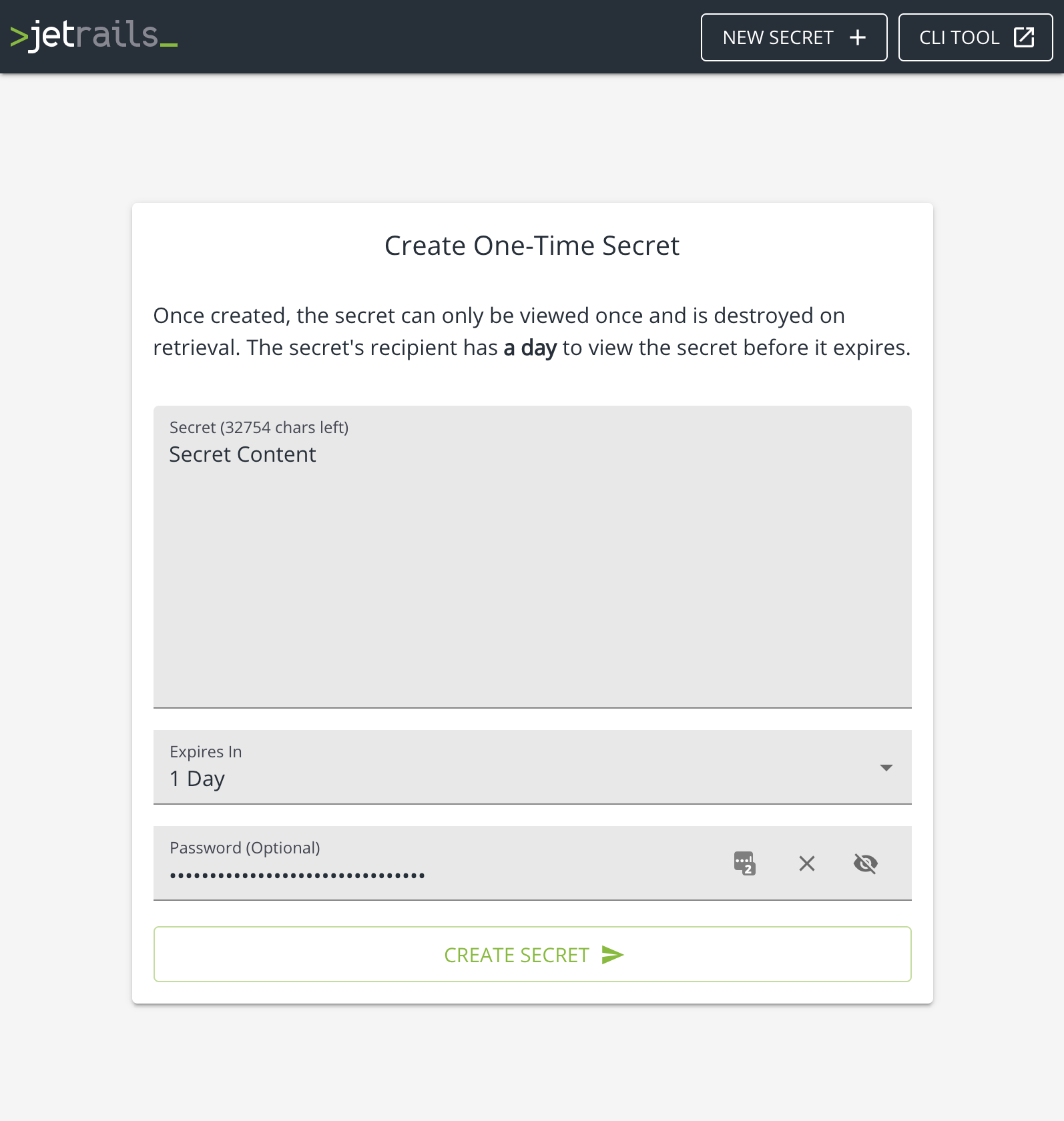
The next section that is displayed shows the details of the secret. Notably, the URL to view the secret. Clicking on the Burn Secret button will delete the secret.
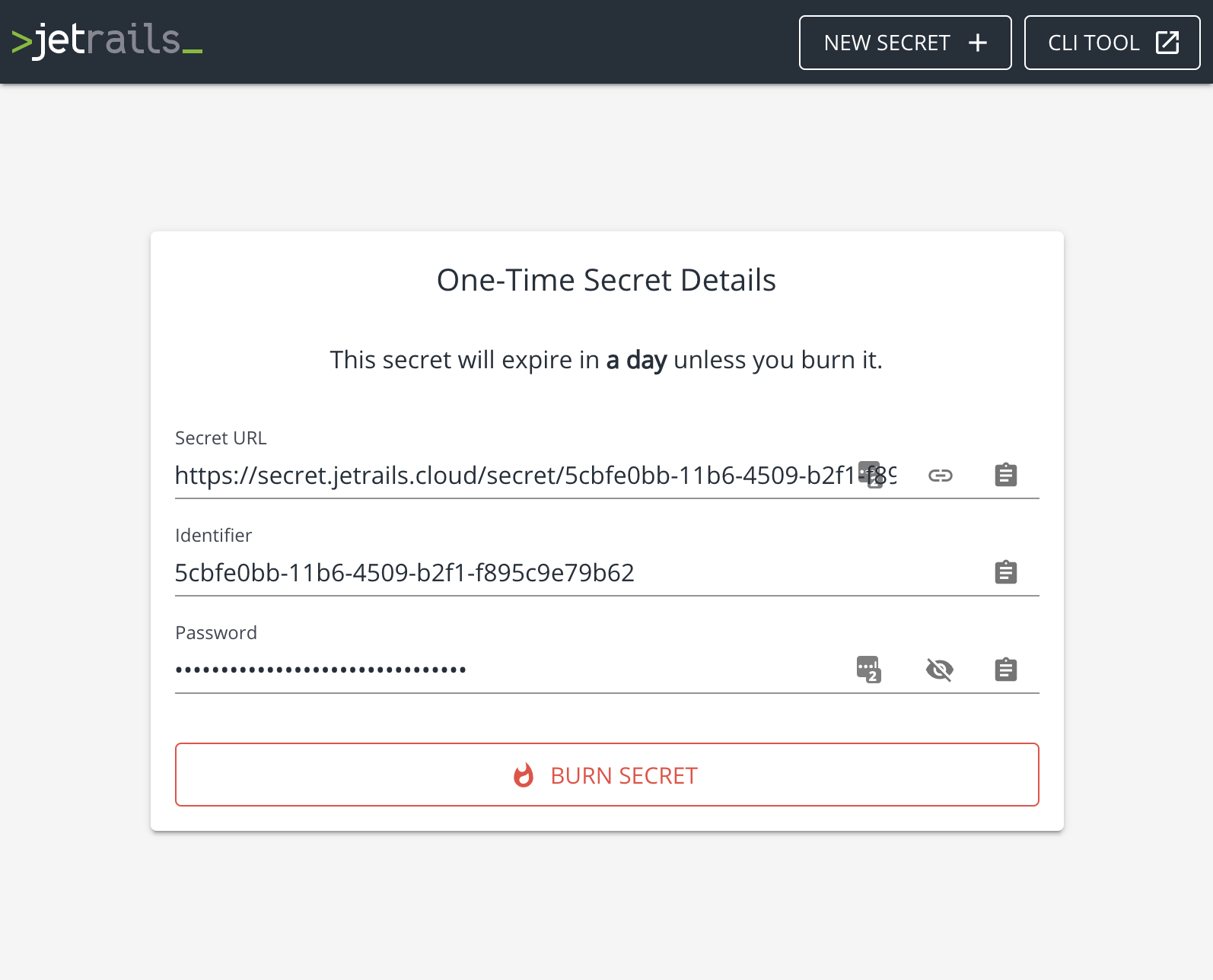
Once the recipient of the secret navigates to that URL, they will be greeted with a password prompt (if the secret is configured with a password).
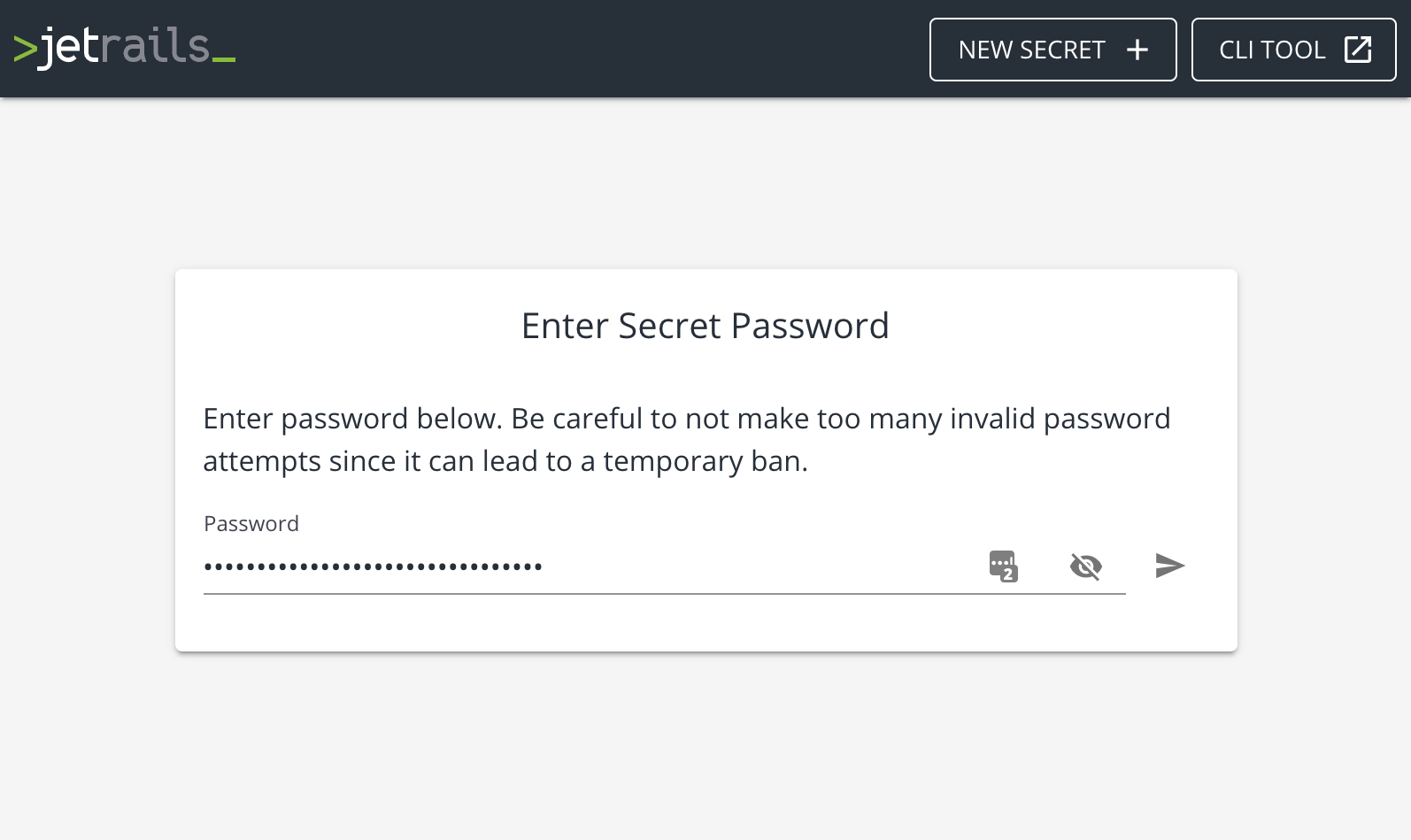
If the password is valid, then the contents of the secret is displayed. Revisiting that link will result in a failure to find the secret since it was already seen.
Using our CLI tool
The One-Time Secret service is available to use through the jrctl CLI tool. Please refer to the project’s documentation for installation instructions. If you are using MacOS, then you can install it through brew:
$ brew tap jetrails/tap
$ brew install jrctl
$ jrctl -v
A simple example on how to interact with the service through our CLI tool can be found here. While the options for creating a secret are more robust, we will show how to use the contents of a file as the secret contents:
Once created, the intended recipient of the secret can view the secret contents with the following command:
For more information, refer to the help menu in the CLI tool.
Using our API
Optionally, you can use our API to create, read, and delete secrets. Our API is open to the public and while it is rate-limited, it does not require any authentication to use.
The following CURL command can be used to create a secret, note that the ttl parameter is optional and defaults to one day. If auto_generate is true then the password field is not used and a password is generated server side and returned.
$ curl https://api-public.jetrails.com/secret \
-X POST \
-H "content-type: application/json" \
--data-binary '{"data":"Secret Content","auto_generate":false,"password":"8os1keTPvZDVPLypAv0YWyPqMKzZAtmA","ttl":86400}' \
| jq
{
"id": "ea9d0ff1-734e-4886-aad4-bbc2bcea800b",
"password": "8os1keTPvZDVPLypAv0YWyPqMKzZAtmA",
"ttl": 86400
}
To read a secret, simply execute the following CURL command and the secret will be returned in plain text format.
$ curl https://api-public.jetrails.com/secret \
-X GET \
-H "content-type: application/json" \
--data-binary '{"id":"ea9d0ff1-734e-4886-aad4-bbc2bcea800b","password":"8os1keTPvZDVPLypAv0YWyPqMKzZAtmA"}'
Secret Content
Note: If a secret is created without a password, the password property with an empty string must still be passed.
Finally to delete a secret, simply run the following CURL command:
$ curl https://api-public.jetrails.com/secret \
-X DELETE \
-H "content-type: application/json" \
--data-binary '{"id":"ea9d0ff1-734e-4886-aad4-bbc2bcea800b"}' \
| jq
{
"id": "ea9d0ff1-734e-4886-aad4-bbc2bcea800b"
}